Detection and Prevention of Network Intrusion

What is Network Intrusion?
Network Intrusion is recognised as an unauthorised activity. These are the activities that jeopardise the network security and the data available on the network. These days, mostly the new companies and the online brands get attacked. To avoid these attacks, the companies must maintain a team of cybersecurity professionals who can detect and prevent such harmful attacks.
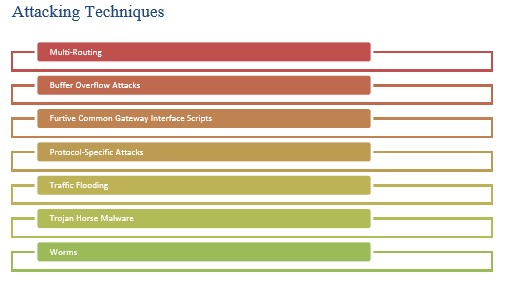
1. Multi-Routing: This is the method which is also called asymmetric routing. It makes more than a single route over the network that is targeted. In this way, the hackers detect a very important portion of the network.
2. Buffer Overflow Attacks: This is a type of attack which overwrites various sections of the memory of a computer present in a network. It replaces the normal data present in a particular location with a command string which is later used for the attack. However, this technique is difficult to attack if there are boundary checking logic that can identify the codes.
3. Furtive Common Gateway Interface Scripts: The CGI (Common Gateway Interface) helps to make the interaction between the servers and the clients. This is the server that easily provides intruders access the file which is available on the web.
4. Protocol-Specific Attacks: All the devices maintain a list of rules at the time of performing various activities in the network. In this case the protocols including IP, ICMP leave certain loopholes that help in performing the attack.
5. Traffic Flooding: It creates the load of traffic and thus the system fails to screen properly.
6. Trojan Horse Malware: It creates a backdoor of the network and the attackers get access to the network and available data.
7. Worms: This a very easy way for network intrusion. They seek out the information from the network and the systems and transfer the data out from the network.

Detection of Network Intrusion
The Network Intrusion is detected with the help of the Intrusion Detection System (IDS). For the detection process, two methods may be used:
1. Signature-Based Method: In this method, the attacks are detected by the traffic on the network and also identifies the instruction sequence which is very common to a specific malware. The pattern in which it detects is called the signature.
2. Anomaly-Based Method: It uses machine learning to make an activity model. Any new behaviour is compared with this model and any malicious potential declared.

Prevention of Network Intrusion
The Network Intrusion is prevented with the help of the Intrusion Prevention System (IPS). To prevent the intrusion, four types of systems may be used:
1. Network-Based Intrusion Prevention System: It scans the whole of the network.
2. Wireless Intrusion Prevention System: With the help of wireless network protocols it monitors the activities.
3. Network Behaviour Analysis: It observes the traffic of the network.
4. Host-Based Intrusion Prevention System: It monitors the single host in case of any suspicious activity.
There are several reputed organisations, whose networks can be attacked at any point in time. So, these organisations must hire cybersecurity professionals on cybersecurity who can monitor the networks and save them from any attacks. Important links:
References
https://patents.google.com/patent/US20180324200A1/en
https://dl.acm.org/doi/pdf/10.4108/eai.3-12-2015.2262516
https://patents.google.com/patent/US20190319821A1/en
https://arxiv.org/abs/1901.02672
About the Author
I am Raju Uma Maheshwari from School of Technology pursuing the Higher Diploma in Ethical Hacking and Forensic Investigation Countermeasures. Before starting my course at MDIS I was working as a Manager of Macdanal Granites Pte Ltd, and prior to that I was teaching at a primary school in a small town in Tamil Nadu, India. There was always a plan B for my career development. This plan is to become a professional cybercrime officer. This driving force led me to choose the higher diploma in ethical hacking and forensic investigation countermeasures for my career.
The Management Development Institute of Singapore (MDIS) has a distinctive presence of its own which is attributed to its rich legacy and tradition of excellence. In pursuing my dream of becoming a cybercrime and forensic investigator, MDIS has given me an opportunity to make my dream come true. I enjoy my study at MDIS, the class interactions, teacher’s encouragement in addressing our study concerns and new friends. I am sharing an article on “The Detection and Prevention of Network intrusion” for users’ benefit.