Credential Stuffing and Its Potential Impact

You are your biggest security breach.
As of April 2020, there are 4.57 billion active internet users online, 4.2 billion unique mobile internet users, 3.81 billion active social media users and 3.76 billion active mobile social media users which brings us to a grand total of 16.34 billion users (Statista, 2020). Considering that there are 7.77 billion (WorldoMeter, 2020) people living in the world, that’s twice the number of the entire human population on earth. These 16.34 billion users have different accounts and passwords that could potentially be breached by hackers.

Now, many of you reading this might disagree and say that your social media account providers or your internet banking services have the latest security measures and promised to keep you and your data safe. So what’s there to worry about? True enough, many corporations do have existing security measures set in place to keep your accounts safe, preventing your accounts and passwords from being attacked by malicious hackers.
But, are your passwords different from one another? Do all of your accounts use a different, unique password each containing a different passphrase?
If the answer is no, you are indirectly putting your accounts at risk.
One password for multiple accounts.
Many internet users online use weak or duplicates of their passwords for different accounts across the web. Usually due to being more convenient as well as being less of a hassle coming up with new and strong passwords over and over for every single online account.

Having duplicate passwords on multiple accounts might put you at risk in the form of password attack known as Credential Stuffing.
Credential Stuffing. What is it and how does it affect me?
Credential stuffing is the automated injection of breached username/password pairs in order to fraudulently gain access to user accounts. Large numbers of spilled credentials are automatically entered into websites until they are potentially matched to an existing account, which the attacker can then hijack for their own purposes. (OWASP, 2020)
For example, a particular user has accounts on Gmail, Facebook, Instagram and an online shopping account each sharing the same ID and Password. The online shopping website might have been unsecured and your shopping account credentials got leaked. Here’s where the attacker will strike.
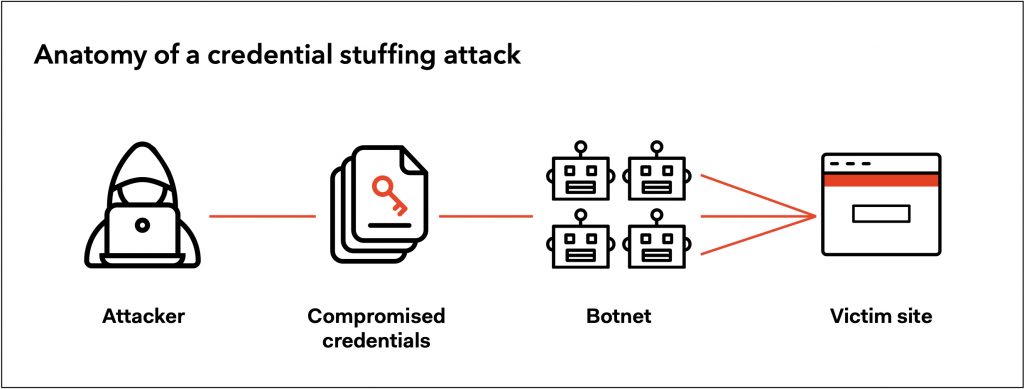
Anatomy of Attack (OWASP, 2020)
- The credentials got acquired by an attacker on a breached website.
- The attacker will then use botnet* to test the stolen credentials against many websites.
- Having gained a successful login (usually 0.1 – 0.2% chance of success). The attacker manages to take over another account with matching credentials.
- The attacker drains the stolen account of stored information/ value.
- The attacker may also use account information for other nefarious purposes.
Botnet* – A botnet is a collection of internet-connected devices infected by malware that allow hackers to control them.
How do I prevent this?
Credential Stuffing can be prevented if proper measures are taken. According to Owasp, here are the methods of prevention. (OWASP, 2020)
- Multi-Factor Authentication
- Secondary Passwords, PINs and Security Questions
- Device Fingerprinting
- Require Unpredictable Usernames
- Block Headless Browsers
Credentials and account security should be your responsibility too.
If proper security measures are taken and malicious websites are avoided. You too can avoid being a victim of Credential Stuffing.










